Notes from the SELinux Developer Summit 2008
The SELinux Developer Summit went pretty well yesterday. It was a long day: 10 hours of talks and discussions with about forty developers attending.
I've just uploaded slides from the talks, which may be found next to their respective entries in the schedule.
Some of the talks I found particularly useful/interesting:
***

Yuichi Nakamura talking about embedded systems and SELinux.
The format worked reasonably well-a series of short talks and discussions-although it would have been nicer to have a more relaxed schedule and more time for deep discussions on specific issues. There's already been discussion of what to do next year, and we may move it to a two-day event. Certainly, I think we'll want to have it again in conjunction with a major developer conference, which makes it a good environment for collaboration with the wider FOSS community.
For those that couldn't make it this year, I believe notes were taken and will be sent out to the mailing list. There are more photos here.
I've just uploaded slides from the talks, which may be found next to their respective entries in the schedule.
Some of the talks I found particularly useful/interesting:
- Josh Brindle on SELinux in Ubuntu. They're making good progress, although the idea of SELinux is to introduce ubiquitous, generalized MAC security, so he is advocating they enable SELinux by default as is done in Fedora, and as you typically do with other OS security layers.
- John Weeks from Sun talking about OpenSolaris FMAC (introducing Flask/TE to their OS). It was interesting to see a dtrace graph of the AVC operating-a kernel mechanism for which I've developed an abstract mental model but never "seen".
- Dan Walsh Talking about his ongoing work in utilizing SELinux to create practical security features for everyday users.
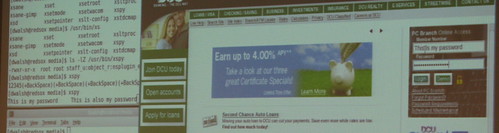
The above is from a demonstration where nsplugin (the framework for Firefox plugins, i.e. where flash etc. is run) is being sandboxed by SELinux, so that a flawed or malicious plugin cannot be used to snoop your keystrokes. In this case, a simulated (and trivial) exploit was blocked from capturing internet banking passwords by SELinux.
Btw, Dan will be demonstrating this today during his OLS talk on Confining the User. There's a lot of really cool stuff coming in this area & the talk should be well worth attending. - Karl MacMillan on alternatives to comprehensive least-privilege, where he described some ideas and plans for simplifying the way SELinux policy is deployed for general purpose use. He has some really promising ideas on reducing the granularity of the policy while still maintaining strong security. This can lead to simpler and smaller policy, which is important for all kinds of users.
- Peter White talked about two higher-level languages being developed to express SELinux policy, Lobster and Shrimp, which will introduce features such as type checking and object orientation to the policy language area. Peter is a Haskell guy, and it all looks very promising.
***

Yuichi Nakamura talking about embedded systems and SELinux.
The format worked reasonably well-a series of short talks and discussions-although it would have been nicer to have a more relaxed schedule and more time for deep discussions on specific issues. There's already been discussion of what to do next year, and we may move it to a two-day event. Certainly, I think we'll want to have it again in conjunction with a major developer conference, which makes it a good environment for collaboration with the wider FOSS community.
For those that couldn't make it this year, I believe notes were taken and will be sent out to the mailing list. There are more photos here.